A while ago I wrote about the permission required to query the status of a Windows service.
Today, I started looking for a way to set this permission from the .NET framework, without using sc or subinacl. Registry and file system security is easy; services, not as much. After what seemed like an eternity of searching I came across the answer - an article on 'stackenbloggen'1 on setting ACLs on Windows services. There is magic in System.Security.AccessControl in .NET 2.0 which lets you control security on pretty much any Windows object, and here are some classes to expose it.
Words can be very specific in the English language, and even more so in code. For example, a method called "SetAccessControl" does not do what it would do if it was called "AddAccessControlEntry". So, if you create an ACE that contains just the item you want to add, and run SetAccessControl, you're screwed.
Never mind, I wrote about how to fix this:
C:\Craig\>sc sdset Service1 D:(A;;CCLS...) [SC] OpenService FAILED 5:Access is denied.
Oops.
Maybe I'll get a better message out of subinacl?
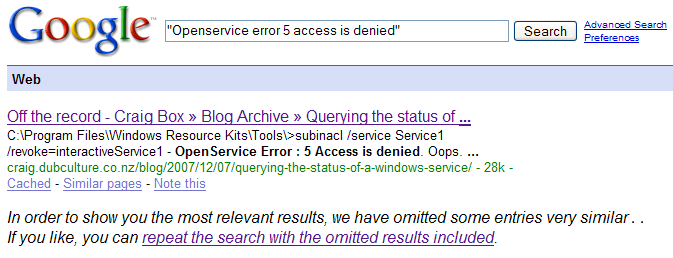
C:\Craig\>subinacl /service Service1 /sacl=D:(A;;CCLS...) Service1 - OpenService Error : 5 Access is denied.
Double oops.
New error message though, worth searching for:
It's very irritating to only find your own post when searching for something! Lots of old-school #wlug'ers used to get this all the time with the WLUG wiki.
A bit more Googling, and the answer is found in Microsoft's knowledge base: how to reset a DACL on a Windows service. The crux of the matter is you need to run a command prompt as LocalSystem - type something like at 15:37 cmd.exe /interactive, where 15:37 is the time one minute from now. (Don't make it bigger. Waiting 30 seconds is tedious enough!)
C:\WINDOWS\system32>whoami NT AUTHORITY\SYSTEM
Booyah!
C:\WINDOWS\system32>sc sdset Service1 D:(A;;CCLS...) [SC] SetServiceObjectSecurity SUCCESS
Double booyah!
I'll be calling GetAccessControl and adding my own ACE to its result from now on, I think.
- I love the name 'stackenbloggen', but a disclaimer that says "[..] my own personal opinions and do not represent my employer's view in any way" is meaningless if you don't say who you are on your blog! ↩
Tags: programming, sysadmin, windows
 Subscribe with a news reader (RSS)
Subscribe with a news reader (RSS) Have new updates sent by e-mail
Have new updates sent by e-mail
Why use "at" to start a cmd.exe as LocalSystem?
Can't you just use runas?
runas /user:Whatever cmd.exe
We used this all the time in my previous job to run tests that needed to run as certain system accounts and such.
"runas won’t work in [this] case, since a process running under an interactive logon session won’t be able to spawn a local SYSTEM process.
For security reasons, only a system process (that is already running as local SYSTEM) like the SCM (services.exe) or RPCSS is allowed to spawn another system process." (source)
Ahh, good link. Thank god for MSDN blogs. I hate to remember doing anything moderately complex in Windows before them.
[...] outro cara já havia passado por isso e deu as dicas de como redefinir uma DACL vazia em um descritor de segurança de um serviço em um [...]