Take Filemon and Regmon, combine them one program (apparently rewriting from scratch), and then change the license to make a previously invaluable sysadmin toolset potentially require payment. Thanks, Microsoft.
Posts Tagged ‘sysadmin’
Microsysinternals releases Process Monitor
Friday, November 10th, 2006Periods in run-parts
Tuesday, October 31st, 2006Repeat after me, Debian/Ubuntu sysadmins. You cannot use the period (.) character in /etc/foo.d directories. Can't can't can't.
Why? Well, man runparts says:
If the --lsbsysinit option is not given then the names must consist
entirely of upper and lower case letters, digits, underscores, and
hyphens.
So, you can't have files named "vhost.foo.co.nz" in your /etc/logrotate.d directory, and you can't have files named "awstats-foo.co.nz" in your /etc/cron.d directory.
As much of a big deal is made of Halloween, and as many groups of kids I saw walking the streets about 7:45, we only had one person knock on the door trick-or-treating. And we managed to successfully pretend we weren't here, sitting in the lounge watching Torchwood. (I keep waiting for the Doctor to turn up.)
Exipick, and importing Apache certificates into IIS
Thursday, October 12th, 2006Greig's cool find of the day:
Exim comes with a script called exipick, which lets you see just the parts of the mail queue that match a particular pattern. ie. we want to get notified of messages that are queued on a backup MX, but aren't just bounces to fake addresses that will eventually time out:
exipick '!$local_error_message'
Which makes looking at mail queues much easier:
root@elston:~# exipick | wc -l 96 root@elston:~# exipick '!$local_error_message' | wc -l 0
My find is a little less interesting, and a little more "just googled it", but if you have certificates in Apache crt/key format, and you want to import them into IIS, you can
do so with openssl:
/etc/ssl/site.net.nz# openssl pkcs12 -export -out site.p12 -inkey site.key -in site.crt
Read more at Michael's meanderings, including about the useful SSLDiag utility.
Windows utilities you didn't know about: dsacls.exe
Wednesday, October 11th, 2006If you set permissions to lock yourself out of an object in Active Directory (or your co-worker does it for you - hi Pete!) then you can use the support tool ADSIEDIT to fix it.
Unless you've done something really difficult, like set DENY permission to "NT AUTHORITY\Authenticated Users".
The error was "An invalid directory name was passed" trying to change the properties on the object, which was also showing as a note, and not a container.
A suggestion to update the schema and clear the cache didn't work; what did work eventually, was this gem of a command line, suggested but not entirely correctly spelt out by knowledge base article 300444:
dsacls "CN=Default Global Address List,CN=All Global Address Lists,CN=Address Lists Container,CN=SITE NAME ,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=DOMAIN" /I:T /R "NT AUTHORITY\Authenticated Users"
And they say Windows isn't a CLI OS.
After using /R to remove the ACL, you can use /S to set it back to its inherited-from-parent ACL.
Where did he go?
Thursday, August 31st, 2006I've gone quiet! What have I been doing?
- migrating Cyrus 2.1 with hacked virtual domain support to 2.2 with real virtual domain support. This has been a nightmare and I intend to write a book on it when I get some time.
- helping install and configure the new WLUG blade server
- planning our Software Freedom Day advocacy event
- fixing my blog (thanks Juha)
- fixing Planet WLUG's RSS feed to keep my only reader happy
- hacked me up a sexy "Subscribe to my feed" button
The last three were done in the company of (and with thanks to) Cathy, who now has far less hair.
Slashback
Monday, August 21st, 2006- Regarding reading Windows passwords for future restoration: MVPs have weighed in to suggest it can't be done. Greig has also weighed in with a "why the hell not; obviously something reads the password to see if it matches the one you entered." So, Windows gurus, hack me something unsupported into LSASS.
- Regarding NetworkManager PPTP for Ubuntu Dapper: the previous package didn't work well because it didn't require pptp-linux, but a new package has fixed that, and some build issues, and is now working its way through REVU.
Windows Administrator Challenge: Temporary password changes
Monday, August 21st, 2006I've yet to post something so sensational (or trollworthy, or just "noticed by Digg") to build up a loyal readership of thousands. I'm sure it'll come eventually. I need to do a couple of things: pimp myself to various Planets, and decide exactly what it is I write about. Generally, it's "things related to what I'm working on", which may or may not be of interest.
My last plea for help didn't turn anyone up. Here's another one that hopefully Google will one day turn up for someone who is bored and has the knowledge and skill to do this, or I'll get bored myself, and acquire the knowledge and skill to do it. Perhaps when it's cricket season again..
I want a simple add-on for the Active Directory Users & Computers MMC utility that does the following things:
- Allows you to change a password for a user, and more importantly
- Saves the original password, so you can reset it later.
No more will you have to ask a user for a password to log into their machine and fix something wrong with their specific profile or operating environment, or change their password and tell them to change it back when you're finished. The script will copy the crypted password to an unused LDAP attribute on the account, and then copy it back when finished - without ever having to know what the password is. By standard means, it's not possible to read the password hash out of AD, so I'm currently seeking help from the newsgroups.
Daniel Petri's help pages have examples on how to extend AD to add options to the context menu for a user, to run VB scripts.
Customising a Debian/Ubuntu installation CD
Thursday, August 17th, 2006One of the things I maintain at work is a self-installing Linux distribution.
When I started in 2002, we were purchasing KickStart installed Red Hat 7.x machines from a local company. With Progeny's AutoInstall, I managed to get a CD that would automatically install Debian Woody, but not in a very nice fashion.
Ubuntu came out, was more up to date than Woody (I think my Commodore 64 was more up to date than Woody for a moment there), and so I changed to it after the second release. Hoary introducted some support for KickStart installations, but I found that much more power could be gained with the new debian-installer that was coming for Sarge. A guide to remastering your Ubuntu CD ensued.
Two releases later, I updated all the machines to Ubuntu Dapper, and tidied up the installer a whole heap. Today, under the chargeable heading of "documenting my self-installing Linux distribution in case I get hit by a bus", I have given the Ubuntu Install CD Customization page a complete overhaul. Read it - it's grand.
Meta-Windows utilities
Monday, July 24th, 2006Want to get all the SysInternals utilities? You can download them all yourself, or there's a really useful SysInternals installer built by Ross Smith II that downloads them all (or the ones you select) and creates shortcuts for them for you.
He also has a similar utility for the NirSoft utilities, which include excellent tools for recovering lost passwords and product keys. Watch out if you run Symantec AntiVirus, as it will suggest they are "hack tools".
Another useful meta-utility is The Ultimate Boot CD for Windows. Built on BartPE, the free and legal Windows LiveCD builder (you must have a license for Windows to use it, and you must not use it on more than one PC at once), The Ultimate Boot CD builds you a bootable image with dozens of useful recovery utilities on it. Every sysadmin should have one.
Graphing and analysing SpamAssassin
Friday, July 21st, 2006Here's something simple that I never thought of - props to my workmate Tom for coming up with this.
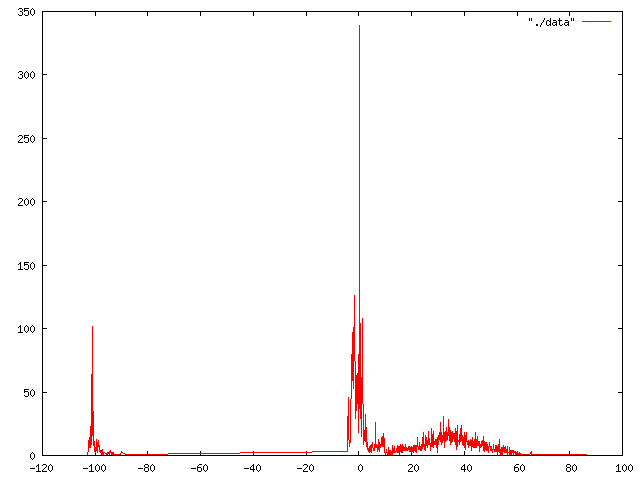
This is a gnuplot graph of our SpamAssassin scores. The code used to generate it is on the bottom of the SpamAssassin notes page at the WLUG wiki.
The grouping around -100 is caused by the whitelist rule, which scores messages down 100 points (ensuring they are never marked as spam). Usefully, this rule doesn't count towards the threshold needed to be reached before a message is learnt as ham by the Bayesian categoriser.
We seem to have a reasonably normal distribution of good mail, between about -5 and +5, and a reasonably normal distribution of spam, between 10 and 60. This means our filter is working really well. What I took from this, is that it was safe to up the ham learning threshold - it defaults to -0.1, but I've set ours to 1, as we have a lot of rules that score all messages up quite equally.
Also useful is sa-stats.pl, which generates a summary table of how often rules were hit on messages that were either marked as ham or spam. As of today:
TOP SPAM RULES FIRED ———————————————————————- RANK RULE NAME COUNT %OFMAIL %OFSPAM %OFHAM ———————————————————————- 1 RAZOR2_CHECK 153 38.65 76.50 1.00 2 BAYES_99 150 37.41 75.00 0.00 3 RAZOR2_CF_RANGE_51_100 149 37.41 74.50 0.50 4 RAZOR2_CF_RANGE_E8_51_100 128 31.92 64.00 0.00 5 URIBL_JP_SURBL 125 31.17 62.50 0.00 6 URIBL_BLACK 120 29.93 60.00 0.00 7 URIBL_SC_SURBL 105 26.18 52.50 0.00 8 URIBL_OB_SURBL 105 26.18 52.50 0.00 9 HOST_EQ_D_D_D_D 102 28.93 51.00 6.97 10 RCVD_IN_SORBS_DUL 92 23.19 46.00 0.50
TOP HAM RULES FIRED ———————————————————————- RANK RULE NAME COUNT %OFMAIL %OFSPAM %OFHAM ———————————————————————- 1 AWL 193 57.86 19.50 96.02 2 BAYES_00 183 45.64 0.00 91.04 3 RELAY_IS_203 78 20.20 1.50 38.81 4 FH_RELAY_NODNS 75 25.44 13.50 37.31 5 HTML_MESSAGE 72 35.66 35.50 35.82 6 UPPERCASE_25_50 60 14.96 0.00 29.85 7 FORGED_RCVD_HELO 56 36.16 44.50 27.86 8 USER_IN_WHITELIST 23 5.74 0.00 11.44 9 NO_REAL_NAME 20 13.22 16.50 9.95 10 SPF_HELO_PASS 19 5.49 1.50 9.45
I toyed with changing the scores on rules that hit lots on both ham and spam, such as FORGED_RCVD_HELO, but they contribute only very small weightings overall at the moment.
 Subscribe with a news reader (RSS)
Subscribe with a news reader (RSS) Have new updates sent by e-mail
Have new updates sent by e-mail